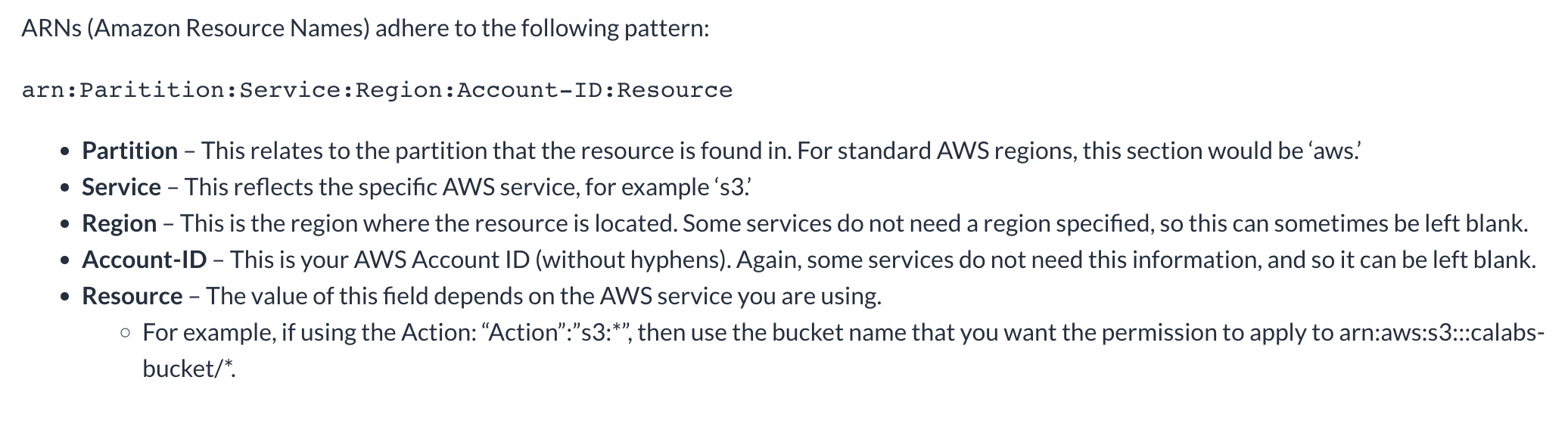
📅 Schedule A Meeting:
In the associated lab we will step through restricting and granting access to specific S3 resources. Our objective is to become more familiar with bucket policies and how they are applied directly to a bucket within S3 itself and apply to that bucket only.
Video Explanation:
Amazon S3 bucket policies and conditions are a powerful tool for controlling access to your S3 buckets and objects. They allow you to specify exactly who can access your bucket and what actions they can perform.
One way to use bucket policies and conditions is to restrict specific permissions for certain users or groups. For example, you may want to allow some users to upload and download objects from your bucket, but not delete them. Or, you may want to allow certain IP addresses to access your bucket, but block all other traffic.
To set up these types of permissions, you will need to create a bucket policy that includes conditions that specify the desired restrictions. The policy should include a statement that lists the permissions you want to grant or deny, along with the conditions that must be met for those permissions to take effect.
For example, to allow certain users to upload and download objects from your bucket, but not delete them, you would create a statement that looks something like this:
{
"Effect": "Allow",
"Principal": {
"AWS": [
"arn:aws:iam::1234567890:user/user1",
"arn:aws:iam::1234567890:user/user2"
]
},
"Action": [
"s3:PutObject",
"s3:GetObject"
],
"Resource": "arn:aws:s3:::my-bucket/*",
"Condition": {
"StringNotEquals": {
"s3:x-amz-request-action": "DeleteObject"
}
}
}
This statement grants the specified users (user1 and user2) the ability to upload and download objects from the my-bucket bucket, but denies them the ability to delete objects. The condition specified in the policy makes sure that the s3:x-amz-request-action is not equals to “DeleteObject”.
Another example, to allow certain IP addresses to access your bucket, but block all other traffic, you would create a statement that looks something like this:
{
"Effect": "Deny",
"Principal": "*",
"Action": "s3:*",
"Resource": "arn:aws:s3:::my-bucket/*",
"Condition": {
"NotIpAddress": {
"aws:SourceIp": [
"1.2.3.4/32",
"5.6.7.8/32"
]
}
}
}
This statement denies all traffic (Principal: “*”) to the my-bucket bucket, unless the request comes from one of the specified IP addresses (1.2.3.4 and 5.6.7.8). The condition specified in the policy makes sure that the traffic is not coming from the IP addresses specified in the list.
Overall, S3 bucket policies and conditions are a powerful tool for controlling access to your S3 buckets and objects, allowing you to specify exactly who can access your bucket and what actions they can perform. With these examples you can easily adapt them to your specific use case and secure your S3 bucket.
Make 💰 By Learning Programming:
- Tesla
- Liquid I.V. Hydration Multiplier 30 Stick, 16.93 Ounce
- Xeela Pre workout
- Sour Strips
- Impractical Python Projects
- Designing Data-Intensive Applications
- Python for Data Analysis
- Python for Data Science Handbook
- Hands-On Machine Learning w/Scikit-Learn & Tensorflow
